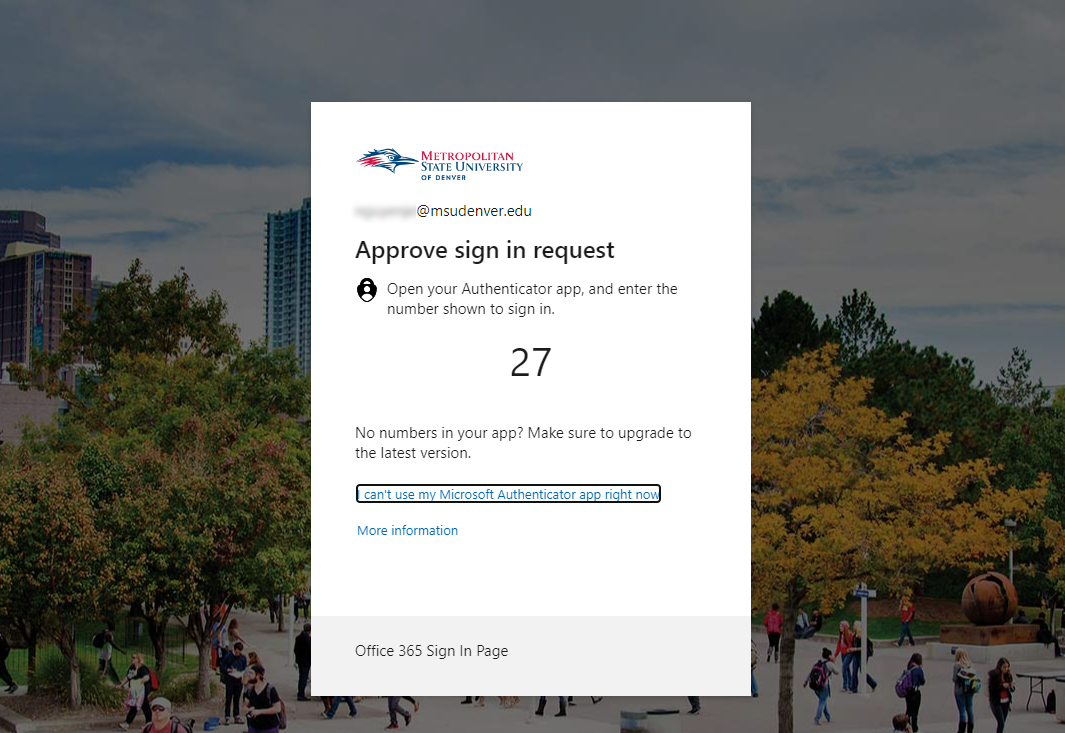
Microsoft will update the multifactor authentication portion of the Office 365 login process Feb. 27. Once applied, Microsoft Authenticator app users will be required to enter a two-digit code to their second factor notification when receiving a push notification. This feature, called number matching, will replace the previous functionality that required only approving a push notification. Users of the Authenticator app who are using a PIN to authenticate will not be affected by this change.
Don’t fall victim to an attack
Microsoft is implementing this feature to combat a rise in multifactor-authentication fatigue attacks. These attacks, also known as “push bombing,” occur when a cyberthreat actor uses stolen login credentials to bombard a user with mobile-app push notifications. Some users may approve one of these fraudulent notifications out of frustration, but others may accidentally approve a fraudulent notification while trying to accept a legitimate one.
Metropolitan State University of Denver’s Information Technology Services Security Team has seen multiple users fall victim to MFA fatigue. For example, an account was compromised using this technique and was then used to send fake job ads through Canvas’ internal-messaging system. With number matching enabled, it will be much harder to accidentally approve a malicious MFA prompt.
The impact for anyone using the Microsoft Authenticator app will be quite broad, as most MSU Denver web services are connected to Microsoft’s Office 365 single sign-on, including:
- Office 365 email
- Teams
- Canvas
- Workday
- WordPress
- GlobalProtect
Other important info:
- Anyone using the Microsoft Authenticator app should ensure that they are running the most up-to-date version, since older versions of the app will no longer work once number matching is live.
- Number matching is not supported for Apple Watch, Android wearable devices or other devices that don’t have a typing interface. Users will need to transition their second authentication factor to a device that supports number-matching prompts.
How to protect yourself
ITS strongly recommends using the Microsoft Authenticator app as your preferred MFA authenticator, especially with this new security feature.
For instructions on making the change, please see How do I switch to using the Authenticator app instead of receiving a phone call? on the ITS Knowledgebase and download and install the Microsoft Authenticator app on the Microsoft support website.
If you have any questions or concerns, please submit an MFA Support ticket.
Additional resources
- What is Multi-Factor Authentication? (Source: MSU Denver ITS Knowledgebase)
- Advanced Microsoft Authenticator security features are now generally available (Source: Microsoft)
- Defend your users from MFA fatigue attacks (Source: Microsoft)
- Implementing Number Matching in MFA Applications (Source: Cybersecurity & Infrastructure Security Agency, cisa.gov)